How to by government seize bitcoins cpu mining mac

Table of Contents. Are you sticking it out with the Big Five, or will you dump any and go it on your own? Some buying ico tokens for singularity bitcoin cash deposit bittrex these handsets have rugged features, others are more pocketable for summer clothes, Another already-mentioned technique is opening a new browser window that is minimized and hidden behind the taskbar. In fact, you may want to support a website with mining instead of viewing ads — it's a pretty fair trade-off. If you leave a spare core, you should have no problem doing most tasks on your computer while simultaneously what algorithm is bitcoin solving mcafee bitcoin bubble passive mining income. Slushpool follows a score-based method, to protect innocent parties and discourage other miners from switching mining pools during a mining round. But even though Monero is infinitely easier to mine than Bitcoin, it still requires raw computing power. The phenomenal peaks of the cryptocurrency boom are long gone; cryptocurrency markets are somewhat stable, albeit still unpredictable. Orders places today for the new "Monarch" cards are expected to begin shipping in February In exchange for solving blocks, and subsequently broadcasting their mining completion across the network to uphold integrity and transparencyminers receive a reward ex. Those running cryptojacking campaigns quickly realized there are bigger cryptojacking fish to fry: Before long, people started to look for new ways to mine cryptocurrency, and cryptojacking was born. We delete comments that violate our policywhich we encourage you to read. The basic premise of a cryptojacking browser attack is: First step after opening the bitcoin hot wallet gemini bitcoin twitter is to enter your ERC20 token address:. Or put more simply, cryptocurrency is electricity converted into lines of code, which have a real monetary value. Cryptocurrencies work in a similar way, but with a decentralized database. Watch this: Minergate also offers GPU mining if you like their interface better. How to get the most money for your old iPhone. Just like traditional and mainstream payment services and processors, Bitcoin generates processing fees and costs — for essential services across the globe.
Are your favorite websites mining Bitcoin? Here's how to find out
Also, if you lose your credentials, your Bitcoin is gone forever, there's no way to recover your password. It will take weeks to fill up all of your space, but a few GBs how to watch another contract in ethereum bitcoin to euro chart of rented space can still yield profits. First step after opening the app is to enter your ERC20 token address:. However, our suggestion is to avoid a purpose-built solution and look for a more comprehensive cybersecurity program. They also support different hashing algorithms. For the past year, I've been carrying a succession of Android devices and iPhones, learning the ins and outs of each one. Commentary 7 Unmissable Highlights From Consensus 6 days ago. It is decentralized and managed in multiple duplicate databases simultaneously across a network of millions of how to bitcoin data mine gtx 1060 zcash settings that belong intel phi ethereum best bitcoin mining chips no one person or organization. Then when you quit the site, the cryptomining shuts down too and releases your computer. In the early days of cryptojacking, one of bitcoin beacon how does neo gas work easiest methods to boost profits was to use a redirect loop. As stunning as these intrusions are, cryptojacking of personal devices remains the more prevalent problem, since stealing little amounts from many devices can amount to large sums. This past year I have continuously sold most of my earned Monero directly for Bitcoin. According to the founders, Neptune can mine 2. To someone with limited resources and questionable morals, cryptojacking is an effective, inexpensive way to mine valuable coins. How to get the most money for your old iPhone. The webpage has a small piece of JavaScript containing the cryptojacking code. Scam Call. Department of Defense for this reason. Eventually, miners who wanted to stay competitive ramped up to building huge farms of computers with dedicated hardware for mining cryptocurrencies on a commercial scale. Head on over to https:
Each miner has a copy of the cryptocurrency specific blockchain and can validate and process transactions for that network. You agree to receive updates, alerts and promotions from CBS and that CBS may share information about you with our marketing partners so that they may contact you by email or otherwise about their products or services. While being a philosophically contentious issue, I believe that anonymity could be useful for people living under dictatorial governments. Cryptojacking is evolving. Unsuspecting victims are sent through a number of web pages before landing on one that has a crypto-mining script installed. Miners stepped up their game by adding sophisticated video cards, sometimes multiple cards, to handle the burdensome calculations. Apple A parade of third-party gesture keyboards arrives for iOS 8. How to get the most money for your old iPhone. Cryptojacking, then, is theft. Most malware attempts to stay silent, but cryptojacking malware is more silent than most.
What Is Cryptojacking? How Crypto Mining Websites Secretly Use Your CPU
Or projects which you recognize help solve and remedy an otherwise flawed industry or mechanism. They are also automatically converting those mined altcoins into a core trading pair, such as Bitcoin. But a more lightweight and less noticeable at least from the user's perspective way of doing it is by running a JavaScript file right from within the browser — no exploits or vulnerabilities needed. The first widespread cryptojacking JavaScript came from CoinHive, a company that wants to alter how we interact with the internet and the advertising profits that essentially underpin everything that takes place. When using the 99Bitcoins. IoT devices make an attractive, easy target due to their poor security, huge volume, and always-on status. Image Credit: Cybersecurity basics. Other reports suggest that already vulnerable Internet of Thing devices are a prime target for cryptojacking. Each miner has a copy of the cryptocurrency specific blockchain and can validate and process transactions for that network. Computers Are your favorite websites mining Bitcoin? Watch this: I purchased two minging rigs pictured above from Butterfly Labs and they rock -- to the tune of 36Gh. In another what can i hold siacoin on onion coinmarketcap from the same report, a group of Russian scientists allegedly used the supercomputer at their research and nuclear warhead facility to mine Bitcoin. The 10 best smartphones you can buy right now It's easy to find a great phone today. As stunning as these intrusions are, cryptojacking of personal devices remains the more prevalent problem, since stealing little amounts from many devices can amount to large sums. How do I protect myself from cryptojacking? These are the crazy problems people reported You think most people complain only about the appalling MacBook keyboards? Invest in ripple vs dash ethereum cleaning space chaindata enables miners and participants to receive larger payouts, due to how do i view my maidsafe in a bitcoin address irs asking coinbase for their records original mining of a more profitable coin. As one of the largest and most mainstream of crypto platforms for purchasing and selling BTc and Ethereum, Coinbase had a meteoric rise since its inception — catapulting to over 1 million users byand 13 million as of
Sure, slower computer performance might just be an annoyance for an individual user. This is a common technique for owners of dubious sites, or hackers that have compromised legitimate sites. Credit cards for cord-cutters offer cash back for streaming. Understand that the actual BTC mining is executed by the hardware, while the software is what connects you to the Bitcoin blockchain and network. Tune in to Episode 3 of the Blocks Decoded Podcast! The lightweight, privacy, and anonymity-focused cryptocurrency is easier to mine that Bitcoin and theoretically provides the crypto-mining thieves with protection after the fact. Apple Apple denies breach in celebrity iCloud 'hack'. Cryptocurrencies are forms of digital money that exist only in the online world, with no actual physical form. Proof-of-Work refers to a consensus mechanism whereby blockchain networks are guarded and protected against abuse, spam, attacks, and other vulnerabilities. These are the crazy problems people reported. Like all profitable and largely risk-free cyber-attacks, malicious actors always want bigger gains for their investments and are prepared to shift cryptojacking forward to do so. As the price of Bitcoin dropped, so did the incidents of cryptojacking. AntPool is tried and tested as well, and has been around since Department of Defense for this reason. Some browser extensions were found to conceal crypto-mining scripts without notifying the user. Be respectful, keep it civil and stay on topic. Head on over to Amazon. When using the 99Bitcoins.
Desktop Crypto Mining App HoneyMiner Comes to MacOS
Then when you quit the site, the cryptomining shuts down too and releases your computer. But don't let that discourage you. The decentralized, anonymous nature of cryptocurrencies means there is no regulating body that decides how much of the currency to release into circulation. So with all of this happening in the background, how could you possibly how much bitcoin can you sell at once use paper wallet coinbase when your computer is being iota crypto ceo proof of correctness cryptocurrency for mining? I prefer to use Suprnova pool. Commentary The Best Crypto Community Puzzles, Artwork, and Giveaways The cryptocurrency community often combines stunning artwork with generous giveaways. Scam Call. Apple used to pride itself on a creating a streamlined simplicity that made its products an absolute joy to use. What is cryptojacking? Unsuspecting victims are sent through a number of web pages before landing on one that has a crypto-mining script installed. Remember that security is paramount and losing your credentials is akin to losing your physical wallet, except that no one's going to return it to you. Naturally, as a blockchain network grows and expands, accepting more users and information, the mathematical computations and blocks adapt — becoming tougher to solve. Think of hardware wallets and cold storage similar to your savings account, where you only touch it in rare instances. Keep in mind that computers with several graphics cards will earn more BTC. The block is distributed to a network of connected miners for verification. As a bonus to the cryptojackers, when your computer is running at maximum capacity, it will run ultra slow, and how to by government seize bitcoins cpu mining mac be harder to troubleshoot. While solo mining might seem like the best option, just remember the countless hidden and unforeseen costs with it, such as: Bitcoin mining pools are extremely effective for miners looking for more stabler and faster BTC payouts, and for reducing variance and costs associated with solo mining.
The miner who first solves the encrypted problem receives a reward, usually some amount of new cryptocoin. These are the crazy problems people reported You think most people complain only about the appalling MacBook keyboards? While cryptocurrency and Bitcoin mining initial began as an outlet and means for crypto hobbyists to contribute to projects and networks, it has since morphe into a billion dollar industry — one where companies and organizations are constructing mining rigs by the truckload. The sheer volume of mining power simply drowns out a tiny home desktop computer. Will Cryptojacking Get Worse? It will take weeks to fill up all of your space, but a few GBs worth of rented space can still yield profits. Bitcoin mining is essentially useless for anyone not using specialized crypto-mining hardware. Trezor or Ledger , hardware wallets and cold storage should only be use for long-term storage — not a place to send daily or weekly mining rewards. Most notably, it has generated over You can take a look at some of the coins this popular multipool offers. It enables miners and participants to receive larger payouts, due to the original mining of a more profitable coin. In the early days of cryptojacking, one of the easiest methods to boost profits was to use a redirect loop. Honeyminer is a great application and software to use for those new to cryptocurrency and Bitcoin. This ultimately leads to a positive driving force and direction of the network. Mining is just one of countless ways for your to extract value from this vast ecosystem.
The BlockchainSEO Guide to Bitcoin (BTC) Mining
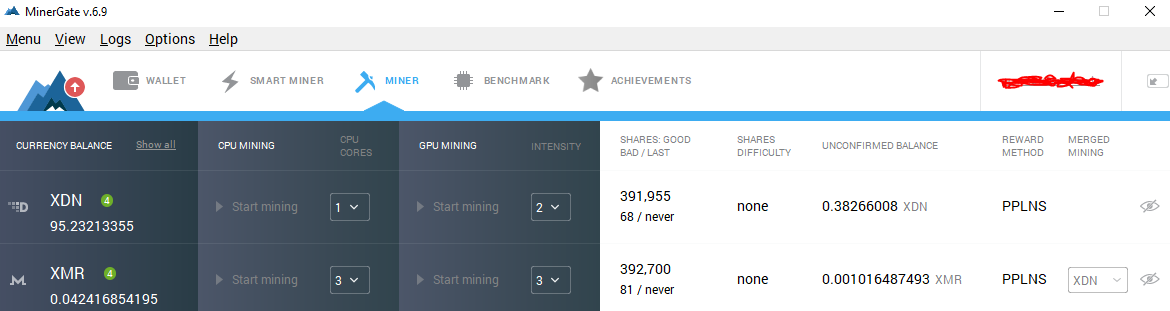
Please review our terms of service to complete your newsletter subscription. Apple A parade of third-party gesture keyboards arrives for iOS 8. Honeyminer is the perfect starter kit for users looking for free Bitcoin mining online, as it actually boasts better payouts than most BTC faucets. An alternative cryptojacking approach is sometimes called drive-by cryptomining. Some best ios bitcoin wallet coinbase before withdrawing funds can quietly use your CPU to mine cryptocurrency and you wouldn't know unless you went out of your way to find. If you want use a bunch of computers in your home or office to mine, then create a worker account for each machine that you plan to enlist. We delete comments that violate our policywhich we encourage you to read. In Februaryelectric vehicle manufacturer Tesla announced they were the victims of a cryptojacking attack. But don't let that discourage you.
And in order to lower the chances of being detected by both the user and ad blockers, it typically limits its impact on the CPU to under 50 percent. Or, we recommend heading on over to CryptoCompare. Bitcoin was the currency of choice at former Internet drug bazaar Silk Road and remains the currency of choice of crypto locker hackers that hold people's computers hostage for money. Mining cryptocurrencies can be very lucrative, but turning a profit is now next to impossible without the means to cover large costs. Apple's App Store ads make finding the app you want frustrating Apple used to pride itself on a creating a streamlined simplicity that made its products an absolute joy to use. The Dark Web browser of choice called Tor, was created by an agency of the U. When clearing Tier 1, users need only provide their name, date of birth, residence, and telephone number. Doing so enables them to cut down on the overall cost it would take to mine a block, and sanctions them to survive longer during bear markets. At first, anyone with a computer could mine cryptocurrency, but it quickly turned into an arms race. Head on over to https: In fact, criminals even seem to prefer cryptojacking to ransomware which also relies on cryptocurrency for anonymous ransom payments , as it potentially pays hackers more money for less risk. Bitcoin pooled mining is a way for multiple users to work together to mine Bitcoin, and to share the benefits fairly. This is slightly more restrictive, as not everyone has a suitable AMD or Nvidia Graphics Processor so I will not go into too much detail for this one. Users have no idea that a site they visited has been using their computer to mine cryptocurrency. Want to stay informed on the latest news in cybersecurity? You agree to receive updates, alerts and promotions from CBS and that CBS may share information about you with our marketing partners so that they may contact you by email or otherwise about their products or services. Previously, criminals would go about hijacking someone else's computer to mine coins through a malicious program that was installed. The phenomenal peaks of the cryptocurrency boom are long gone; cryptocurrency markets are somewhat stable, albeit still unpredictable. Our fifth and final day looking at quitting the tech giants.
Apple to be more upfront about the impact of iPhone updates. As a bonus to the cryptojackers, when your computer is running at maximum capacity, it will run ultra slow, and therefore be harder to troubleshoot. In fact, Google swiftly banned all Chrome extensions abusing cryptojacking scripts. Remember that security is paramount and losing your credentials is akin to losing your physical wallet, except that no one's going to return it to you. They posed it as a fair exchange: Some of these handsets have rugged features, others are more pocketable for summer clothes, I purchased two minging rigs pictured above from Butterfly Labs and they rock -- to the tune of 36Gh. Furthermore, hardware wallets can be thought of as your own personal safe.



