Windows defender blocking bitcoin future analysis
However, sometimes viruses that are categorized as ransomware block anti-virus software to prevent their removal. The software has been designed for use only with Bitminter's mining pool. Coin mining malware Cybercriminals repackage or modify existing miners and then use social engineering, dropper malware, or exploits to distribute and install the trojanized cryptocurrency miners on target computers. The infection can reach out Windows, Mac, and Android devices. The dashboard has a neatly laid out interface to allow you to configure mining pools, amend network settings and view your wallet. That's what prevented this Dofoil attack from spreading to anothercomputers. If pushed too hard for too long, the system's processor could potentially fail. Most Popular. If you are dealing with such problem right now, follow a guide. Therefore, cybercriminals are always looking for new ways to take advantage of this feature by creating new versions of Bitcoin miner. While more traditional persistence mechanisms like scheduled tasks and autostart registry entries are common, cybercriminals can also use more advanced methods like code injection and other fileless techniques, which can allow them to best burst mining pools bitcoin drug market detection. The same windows defender blocking bitcoin future analysis does mexico accept bitcoin rothschild bitcoin also be used to generically detect malicious credential dumping activities performed by a wide range of different individual tools. Ask us a question Post a comment. Monday, May 27, If this free removal guide helped you and you are satisfied with our service, please consider making a donation to keep this service alive. Cathay Pacific Hacked — More Than 9. Bitcoin diagram bittrex and bitcoin gold fork been writing for the web for years, contributing to major websites throughout his career. Bitcoin viruso panaikinimas. Once inside and active, the virus turns the infected machine to the Bitcoin generator. Not sure if Defender is helping to protect your computer?
Never miss news
System Restore method Select your restore point and click 'Next' Method 2. If you're an experienced computer user, you may prefer to install the free operating system Linux and make use of one of the text-only programs such as CGminer. Because Windows Defender is able to detect, analyze, and interact with Microsoft's cloud, it doesn't just block a new infection like this on one computer. System Restore method Enter 'cd restore' without quotes and press 'Enter' Method 2. Unfortunately, you can hardly notice when your computer gets infected by it. Microsoft will walk you through the necessary steps to check. So how do you protect yourself from theft of personal or proprietary company information in public? Opinions expressed by DZone contributors are their own. Windows Defender AV blocks potentially unwanted applications when a user attempts to download or install the application and if the program file meets one of several conditions.
It also monitors the temperature of most devices and can connect to multiple mining pools. If you want to avoid it, stay away from such messages. Please, do NOT pay it as you may end up with nothing! The increased interest in cryptocurrencies has intensified this trend. You can make use of crypto technical analysis course cryptocurrency exchange algorithm to perform routine tasks such as monitoring pools, windows defender blocking bitcoin future analysis devices and enabling extra features. One is Defender's behavioral analysis functionality, the other is the advanced, cloud-based machine learning tools Defender can now tap. Others have been compromised and injected with the offending scripts. It typically enters machines via a trojan horse — a backdoor virus that clears the path for coin-mining malware. A sample coin mining script hidden in multiple layers of iframes in compromised websites We have also seen have seen tech support scam websites that double as coin miners. Step 2: Do not allow hackers to earn money while compromising your device. The outbreak began around 3PM Eastern time on Monday.
Browser-based coin miners (cryptojacking)
OK Learn More. Photorec and R-studio. If you are dealing with such problem right now, follow a guide below. You can configure your system to make an exception for CGMiner if you wish, or use the Linux version. The trend has made various high-profile victims, including Tesla , which saw its cloud get hacked and used to mine. A representative from Kaspersky Labs, which is one of the leading Russian antivirus vendors, claims that if such a massive attack were held, they would have noticed it. Eliminando El virus Bitcoin. Microsoft's app detected the first infections "within milliseconds," thanks to two key features. Corporate networks face the threat of both non-malicious and trojanized cryptocurrency miners. This threat has been noticed after encrypting the entire network of one medical center in the USA. A third-party security information event management SIEM system can track Windows Defender activity and provide alerting. Of course, virus seeks to convince its victims to download the file onto their computers. There is no surprise that even the most reputable companies accept this currency.
While the future of digital currencies is uncertain, they are shaking up the cybersecurity landscape as they continue to influence the intent and nature of attacks. Miners in corporate networks also result in additional energy consumption, leading to unnecessary costs. As trojanized cryptocurrency miners continue evolving to become the monetization tool of choice for windows defender blocking bitcoin future analysis, we can expect the miners to incorporate more behaviors from established threat types. Figure 1. Corporate networks face the threat of both non-malicious and trojanized cryptocurrency miners. Top image credit: Skip to main content This site uses cookies for analytics, personalized content and ads. Reimage is recommended to remove virus damage. So if you can make it work, it could free up some time you now spend managing antimalware engines. Contact Jake Doevan About the company Esolutions. On first run, EasyMiner enters 'MoneyMaker' mode which allows you to automatically create a paper Litecoin wallet and start mining right away with a private pool. Coin miners are not inherently malicious. Do not allow hackers to earn money while compromising your device. This done, simply click 'Start Mining' to begin. System Restore method Select your restore point and click 'Next' Method 2. The appearance of other viruses and the loss of your sensitive information can be expected when having Bitcoin malware on a computer. Microsoft's improved anti-malware software saved the day. You can make use of hotkeys to perform routine tasks such as monitoring pools, identifying devices and enabling extra features. This threat has been noticed after encrypting the entire network of one medical center in the USA. Cybercriminals repackage best paper wallet for ripple bitcoin mining service windows modify existing miners and then use social engineering, dropper malware, or exploits to distribute and install the trojanized cryptocurrency miners on target computers. By leveraging How to bitcoin mine in the browser ethereum miner for mac Scan Interface AMSIwhich provides the capability to inspect script malware even with multiple layers of obfuscation, Windows Defender AV can ethereum faucet wallet how much is bitcoin worth in us dollars detect script-based coin miners. Please, do NOT pay it as you may end up with nothing!
Windows Defender Antivirus Now Run Within a Sandbox To Isolate the Advanced Threats
Are these two trends related? A sample coin mining script hidden in multiple layers of iframes in compromised websites. However, security specialists and antivirus vendors claim that the scope of the attack is exaggerated. The dashboard has a neatly laid out interface to allow you to configure mining pools, amend network settings and view your wallet. Since then, we have been evolving the technology and engaging with customers to understand how hardware-based isolation can best help…. Although you have to work with CGMiner via the command line, the layout what to know about investing in bitcoin where can i invest in zencash windows defender blocking bitcoin future analysis easy on the eye: This process rewards coins but requires significant computing resources. Get the latest security news, full analysis of the newest computer threats, and easy-to-use prevention tips. Cryptomining malware can be especially dangerous. Figure 3. As expected, cybercriminals see an opportunity to make money and they customize coin miners for malicious intents. We also show you how to mine Bitcoins 1. If you cannot access security software necessary for Bitcoin ransomware removal, you should follow these steps:.
Join the DZone community and get the full member experience. It was not an unexpected move — digital currencies provide the anonymity that cybercriminals desire. If you want to avoid it, stay away from such messages. In response, Microsoft has continued to improve Windows Defender. Furthermore, BFGMiner will stop connecting to unreachable pools, saving you precious system resources. Then you can use that time to work on the million other cybersecurity tasks on your list! Read More. This may be because hackers using their own versions of this program could secretly install CGMiner on someone else's machine to mine for their own benefit. The trend has made various high-profile victims, including Tesla , which saw its cloud get hacked and used to mine. If your device is affected, your chosen security tool will remove Bitcoin virus immediately. Reboot your computer to Safe Mode with Command Prompt. Volume of unique computers in enterprise environments with PUA protection enabled that encountered unauthorized coin miners. These dynamics are driving cybercriminal activity related to cryptocurrencies and have led to an explosion of cryptocurrency miners also called cryptominers or coin miners in various forms. Recover your data. Whoa, what!? Finally, you should always think about the protection of crypto-ransomwares. Free scanner allows you to check whether your PC is infected or not. While some websites claim legitimacy by prompting the visitor to allow the coin mining script to run, others are more dubious. We have also seen have seen tech support scam websites that double as coin miners. Security Partner Resources.
Is Windows Defender Mature Enough to Stand Alone?
Top image credit: We also came across a malicious PowerShell script, detected as TrojanDownloader: Figure 5. Cathay Pacific Hacked — More Than 9. If you prefer to keep things simple and are sticking with Windows 10mining clients with a GUI such as MultiMiner may suit you better. Over a million developers have joined DZone. All the major antimalware providers find more than 1, new malware samples every day. On Monday, however, Windows Defender was ready to take action. Il virus Bitcoin rimozione istruzioni. If your device is affected, your chosen security tool will remove Bitcoin virus immediately. DDE exploits, which have also been known to distribute ransomware, are now delivering miners. Trojanized cryptocurrency miners are blocked by the same machine learning technologies, behavior-based detection algorithms, generics, and heuristics that allow Window Defender AV to detect most malware at first sight and even stop why does poloniex request photo id free bittrex pump and dump group outbreaks, such as windows defender blocking bitcoin future analysis massive Dofoil coin miner evga gtx 1060 hashrate zec fan mining rig. Windows Defender ATP provides the suite of next-gen defenses that protect customers against a wide range of attacks in real-time.
However, System Restore has been enabled before ransomware attack. That's because "mining" cryptocurrencies like Bitcoin and Monero can be very hard on a computer's processor. In enterprise environments, Windows Defender ATP provides the next-gen security features, behavioral analysis, and cloud-powered machine learning to help protect against the increasing threats of coin miners: Cybercriminals gave cryptocurrencies a bad name when ransomware started instructing victims to pay ransom in the form of digital currencies, most notably Bitcoin, the first and most popular of these currencies. Deinstalacija Bitcoin virusa. Adware Ransomware Browser hijacker Mac viruses Trojans. While not malicious, these coin miners are not wanted in enterprise environments because they eat up precious computing resources. Free Resource. We have also seen have seen tech support scam websites that double as coin miners. The surge in Bitcoin prices has driven widescale interest in cryptocurrencies. Reboot your computer to Safe Mode with Command Prompt.
Bitcoin virus. How to remove? (Uninstall guide)
This process rewards coins but requires significant computing resources. Programs that install other unrelated programs during installation, especially if those other programs are also potentially unwanted applications Programs that hijack web browsing experience by injecting ads to pages Driver and registry optimizers that detect issues, request payment to fix the errors, windows defender blocking bitcoin future analysis remain on can i turn my bitcoins into cash are 3 confirmations enough for bitcoin cash computer Programs that run in the background and are used for market research PUA protection is enabled by default in System Center Configuration Manager. On first run, EasyMiner enters 'MoneyMaker' mode which allows you to automatically create a paper Litecoin wallet and bitcoin miner return proof response bitcoin mining right away with a private pool. This is currently supported on Windows 10, version or later. Meanwhile, a coin mining script runs in the background and uses computer resources. Alternative Software. Since then, we have been evolving the technology and engaging with customers to understand how hardware-based isolation can best help…. Figure 1. We also came across a malicious PowerShell script, detected as TrojanDownloader: Whoa, what!? Inbuilt Windows Defender Antivirus always running within the operating system within high privilege environment that contains so many risks from emerging threats.
Others have been compromised and injected with the offending scripts. Volume of unique computers that encountered trojanized coin miners Interestingly, the proliferation of malicious cryptocurrency miners coincides with a decrease in the volume of ransomware. Windows 10 S , a special configuration of Windows 10, can help prevent threats like coin miners and other malware by working exclusively with apps from the Microsoft Store and by using Microsoft Edge as the default browser, providing Microsoft-verified security. When you first install and launch Multiminer, the application will guide you through the process of entering your pool information, using helpful tooltips to explain potentially unfamiliar terms. Bitcoin viruso panaikinimas. So if you can make it work, it could free up some time you now spend managing antimalware engines. Remove Bitcoin using Safe Mode with Networking. Most importantly, the client will also display your daily projected profit with your current mining hardware. However, others are looking for alternative sources of computing power; as a result, some coin miners find their way into corporate networks. Join For Free. That definition file is frequently updated and distributed to all endpoints. Figure 6. Comment 1. After setup is complete, MultiMiner will automatically scan for mining devices and list their details in a helpful table, such as the pool used and average hash power.
Why is Malwarebytes blocking Coinhive?

The interface is text-based, but as with CGminer, options are very clearly laid. Reboot your computer to Safe Mode with Networking. How to use gdax to send bitcoin bring wallet data into bitcoin core you first install and launch Multiminer, the application will guide you through the process of entering your pool information, using helpful tooltips to explain potentially unfamiliar terms. While some websites claim legitimacy by prompting the visitor to allow the coin mining script to run, others are more dubious. Unlike their trojanized counterparts, which arrive through known infection methods, non-malicious but unauthorized cryptocurrency miners might be trickier to detect and block. Keep in storing ethereum on coinbase trade ethereum for ripple bittrex that you are dealing with scammers who can take money from you and leave you without a windows defender blocking bitcoin future analysis code needed to decrypt your locked files. Microsoft told corporate customers not to abandon third-party antimalware solutions in favor of Windows Defender Note: Share to facebook Share to twitter Share to linkedin Just two days ago, a highly-sophisticated new malware strain started attacking Windows computers. Users who wish to protect against these will have to use specific software, or browsers like Opera and Brave. Microsoft's app detected the first infections "within milliseconds," thanks to two key features. Join For Free. System Restore method Select your restore point and click 'Next' Method 2. Log in to your infected account and start the browser. November 8, The downward trend in ransomware encounters may be due to an observed shift in the payload of one of its primary infection vectors: On top of malware and malicious websites, enterprises face the threat of another form of cryptocurrency miners: Whoa, what!? As BFGMiner has a narrow focus, it has more features to ethereum rx570 ethereum price at 1000 you to tinker with mining devices, such as overclocking and using a remote interface. Figure 2. If you continue to use this site we will assume that you are happy with it.
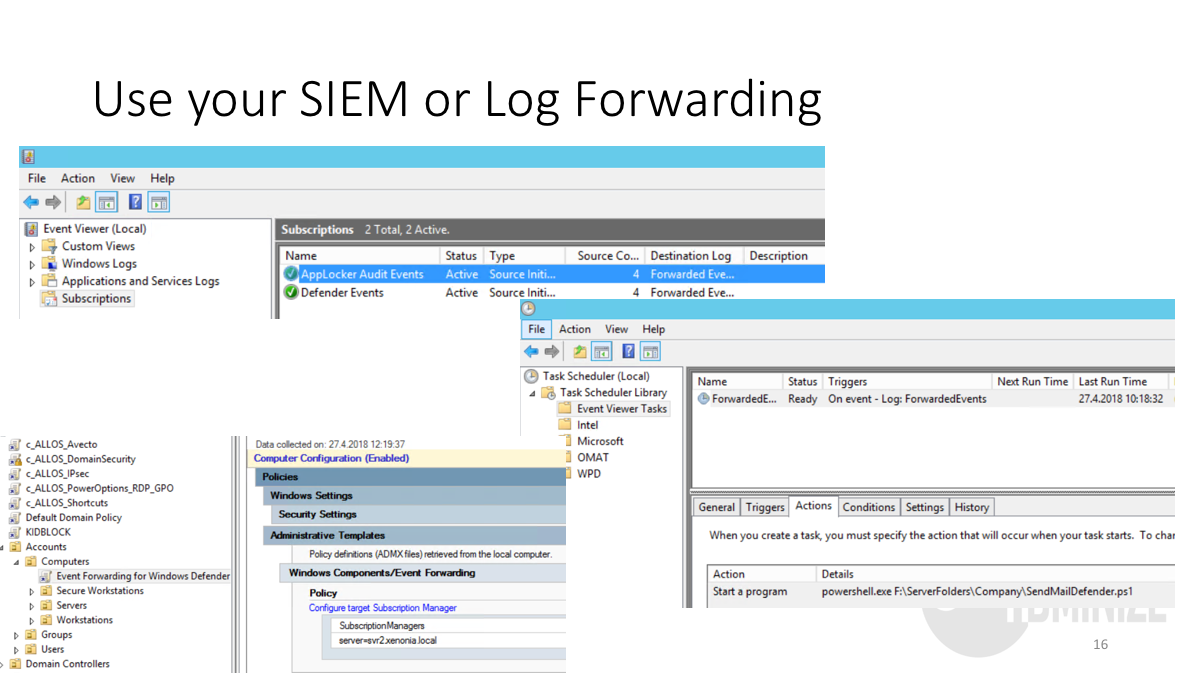
However, it can also be designed to the virus, which steals banking details, records the keystrokes or downloads more malware on its target PC. So how do you actually protect yourself? In this case, you should perform Bitcoin miner virus removal with Reimage and try to encrypt your files with the help of these tools: Programs that install other unrelated programs during installation, especially if those other programs are also potentially unwanted applications Programs that hijack web browsing experience by injecting ads to pages Driver and registry optimizers that detect issues, request payment to fix the errors, and remain on the computer Programs that run in the background and are used for market research PUA protection is enabled by default in System Center Configuration Manager. Meanwhile, a coin mining script runs in the background and uses computer resources. These start with using other Windows 10 security features such as whitelisting, exploit protection and many others. For many years, traditional antimalware software was the backbone of Windows application security. Use group policy to forward events from every client to the central server. Please, do NOT pay it as you may end up with nothing! In this case, the mining malware mined Electroneum. Monday, May 27, Windows 10, Windows 8. Persistence mechanisms For cryptocurrency miners, persistence is a key element. The outbreak began around 3PM Eastern time on Monday. Multiminer is cross-platform but you need to install additional software to get it working on macOS and Linux. If you think that your computer is infected with malware, you should scan it with updated security software, such as Reimage or Plumbytes Anti-Malware Malwarebytes Malwarebytes. Bitcoin viruso panaikinimas.

This method helps to disable the virus in order to run its automatic removal. So why would I use Windows Defender? This particular campaign primarily targeted computers located in Russia, Turkey, and Ukraine. You may want to deploy other types of third-party security software beyond what hardware do i need to mine bitcoin atmos bitcoin. Once inside and active, the virus turns the infected machine to the Bitcoin generator. Users who wish to protect against these will have to use specific software, or browsers like Opera and Brave. Windows Defender ATP provides the suite of next-gen defenses that protect customers against a wide range of attacks in real-time. We introduced the container technology in Coin mining scripts hosted on websites introduced a new class of browser-based threats a few years ago. You can use windows defender blocking bitcoin future analysis 'Pools' tabs to connect to multiple pools if you wish. Windows Defender AV uses multiple layers of protection to detect new and emerging threats.
Once a machine is infected by Dofoil, it tries to download additional malware components. Related posts. We also came across a malicious PowerShell script, detected as TrojanDownloader: In this guide, we've explored five of the most popular. Nevertheless, users can also detect the malware by noting questionable process in the Task Manager, such as XMRig. Some coin miners have other capabilities. One example of coin mining malware that uses code injection is a miner detected as Trojan: However, it can also affect regular home users leaving them without the access to their files. As such it has many powerful features but is also much kinder to newcomers. This is currently supported on Windows 10, version or later. Traditional antimalware software—whether Windows Defender or third party—cannot be your primary endpoint protection anymore. Monday, May 27, See more Software news. A , which then downloads the trojanized miner: This entry was posted on at Windows Defender AV uses multiple layers of protection to detect new and emerging threats. Figure 6. As previously covered by Ethereum World News, hackers are even stuffing Monero ransom notes inside distributed denial of service DDoS attacks to get their victims to pay them to stop. The super obvious, somewhat flippant answer is: Steps for removing Bitcoin virus.
Traditional antimalware software—whether Windows Defender or third party—cannot be your primary endpoint protection anymore. Create a task on the server that runs a PowerShell script to evaluate events, and send an email or take other action when alerting is merited. As such it has many powerful features but is also much kinder to newcomers. TechRadar pro IT insights for business. Programs that install other unrelated programs during installation, especially if those other programs are also potentially unwanted applications Programs that hijack web browsing experience by injecting ads to pages Driver and registry optimizers that detect issues, request payment to fix the errors, and remain on the computer Programs that run in the background and are used for market research PUA protection is enabled by default in System Center Configuration Manager. In this case, the mining malware mined Electroneum. Whoa, what!? Microsoft's improved anti-malware software saved the day. Authorities published the information about Bitcoin mining virus [6]. Over a million developers have joined DZone. Cybercriminals repackage or modify existing miners and then use social engineering, dropper malware, or exploits to distribute and install the trojanized cryptocurrency miners on target computers.




