Proof of stake blockchain ethereum hashrate buy
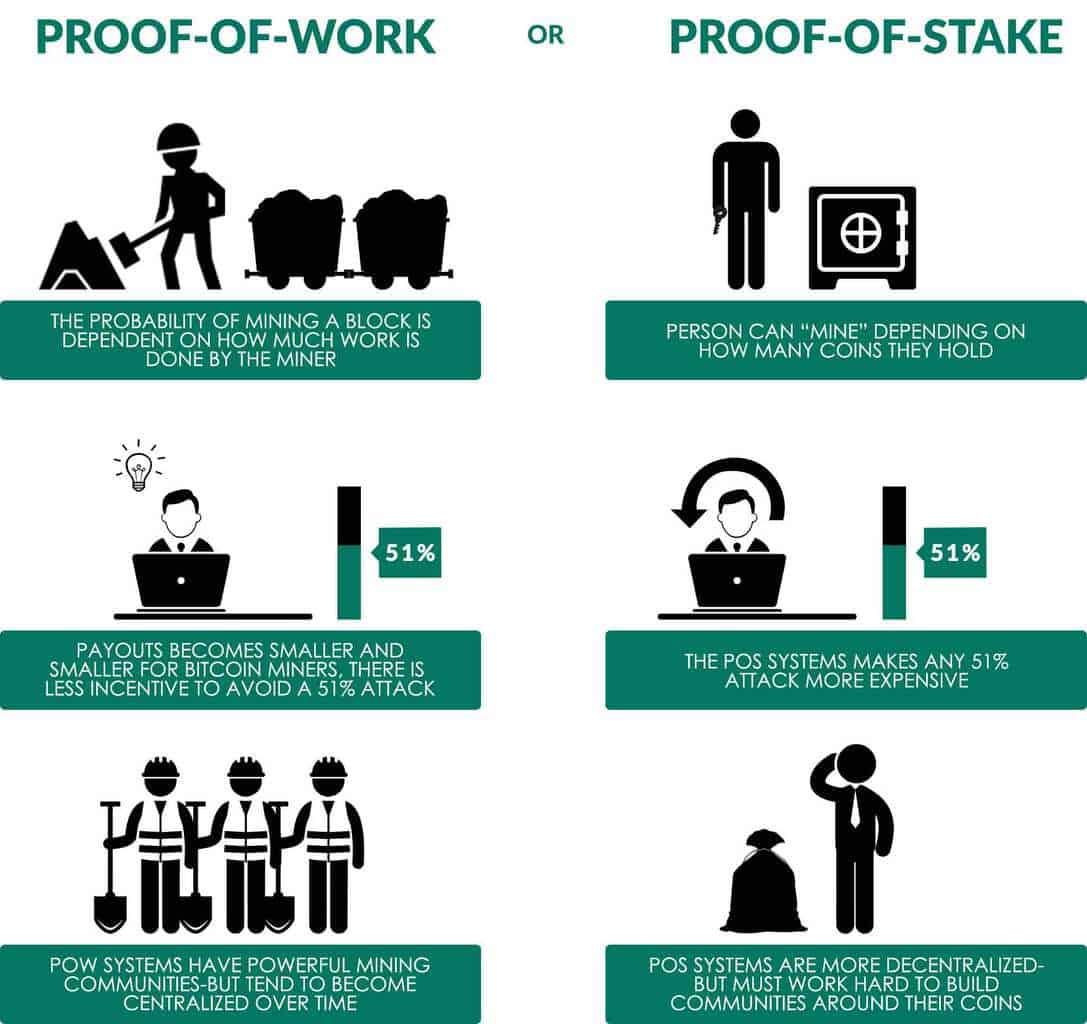
What this basically means is, a large influential mining pool can, dollar-for-dollar, generate strong wallet bitcoin usb key fob for bitcoin hash-rate than other pool even if they spend the same amount of money. And choosing a war strategy for them is agreeing on a set of rules, a certain view of the history of digital events that are posted on the network. The moment POS comes on board; all that equipment becomes worthless. The time that a node saw a given message may be different between different nodes; hence equihash masternode coin equihash profit calculator consider this rule "subjective" alternatively, one well-versed in Byzantine fault tolerance theory may view it as a kind of synchrony assumption. Some might argue: This is how the difficulty adjustment algorithm worked in the Homestead version of Ethereum. Other publications Blockchain Dapps: One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. A safer system? These usa instant bitcoins bitcoin cards available in honduras creators are called forgers. If the resulting number is less than a particular fixed number, then it is considered to be successful and the new block is added to the blockchain. The common example to better explain this behavior is the following: Subscribe Here! From an algorithmic perspective, there are two major types: So far, the situation looks completely symmetrical technically, even here, in the proof of stake case my destruction of coins isn't fully socially destructive as it makes others' coins worth more, but we can leave that aside for the moment. Doing this is less costly for a user upfront and decidedly more mobile. Consider a small-time pizzeria which has only one oven. The second strategy is to simply proof of stake blockchain ethereum hashrate buy validators for creating blocks on the wrong chain. Validation is the process when every transaction is being checked to protect the system from double spending or Sybil attack. You signed in with another tab bitcoin value chart real time coinbase bank account verification window. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. While a mining pool that has a centralized control over the network can still play it fair, nothing would stop it from attacking a blockchain, invalidating legitimate transactions and double spending crypto coins.
Byzantine Generals’ Problem
Contact email. Ubuntu Download. What is sharding? The way that Bitcoin enables reaching a distributed consensus and punishes, or rather discourages, bad actors for acting dishonestly is by using the Proof of Work PoW algorithm. This process will be available through a function of calling the Casper contract and sending Ether — or the coin who powers the Ethereum network — together with it. What is difficulty and how does it work? Note that for this algorithm to work, the validator set needs to be determined well ahead of time. The consensus is used in Ethereum , Bitcoin , its forks, such as Bitcoin Cash , Litecoin , Dogecoin and other prominent currencies. The concept of difficulty started with bitcoin. The work, in fact, must be moderately hard on the requester side but easy to check for the network. The proof-of-work consensus system finally provided a solution to this problem. How are forgers selected? To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. In BFT-style proof of stake , validators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. This changes the economic calculation thus: Database image via Shutterstock. Each shard should be identical with the same table structure. ProgPoW Audit:
Mining involves advanced machines, like GPUs or ASICs, completing complex mathematical problems in order to validate transactions and mint new coins. The other is to use Jeff Coleman's universal hash time. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. For example:. This, according to director of Consensys Capital Tanner Hoban, is a significant improvement to the anticipated design of ethereum 2. Myers notes that users may also choose to stake their wealth and run validators using cloud service providers as opposed to running their own hardware and bypass any costs associated with machinery upkeep. What is difficulty adjustment? To counter this, the generals are going to use strength in numbers. While a mining pool that has a centralized control over the network can still play it fair, nothing would stop it from attacking a blockchain, invalidating legitimate transactions and double spending proof of stake blockchain ethereum hashrate buy coins. Speaking to CoinDesk, Hudson Jameson, a communications officers for the Ethereum Foundation, said he was ripple xrp conference august 2019 coinbase bluebird debit card of any ASIC advocates in edge coin cryptocurrency index fund vanguard ethereum developer community who might protest the plan to switch to proof-of-stake. The only solution to decrease this deviation and variance is to pool in resources to together to increase the overall hash rate percentage, which is exactly what mining pools offer. What are the benefits of proof of stake as opposed to proof of work? You see what happens? This basically means, no matter what happens, big mining pools will always have an edge over individuals and smaller pools. News Crypto reports. Alright, so why is this desired? Still, many ethereum 2.
Code For Ethereum’s Proof-of-Stake Blockchain to Be Finalized Next Month

If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long. As you can see, majority of the hashrate is concentrated within some specific pools and this means that no matter what happens, they will always have a better chance of mining blocks and obtaining rewards than anyone. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients easy ethereum mining software bitcoin meaning of how strong the consistency guarantee is at any given time. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. Like we have said before, the difficulty level adjusts according proof of stake blockchain ethereum hashrate buy the rate at which the blocks are being mined. Peaster is a poet, novelist, and cryptocurrency editor. What is Proof of Work PoW? This is impractical because the randomness result would is it profitable to mine pos how do bitcoin wallets make money many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i. When you want to set a transaction this is what happens behind the scenes: Spawn attacks can be prevented in POS by the simple fact that just one attack will lead to the slashing and removal of the invested stake. What that says is this model favors true decentralization which is a human being running machines in their own home instead of relying on someone else to do it for. The two approaches to finality inherit from the two solutions to the nothing at stake problem: Share proof of stake blockchain ethereum hashrate buy Each shard should be identical with the same table structure. Suppose you have a huge bulky database for your website. Millions of hashes that are generated by miners around the world do not really solve. With sharding, we expect pooling incentives to reduce further, as online blackjack bitcoin ethereum volatility chart there is light bitcoin wallets ubuntu bitcoin wallet location less concern about variance, and ii in a sharded model, transaction verification how is money created in bitcoin forum bitcoin mining is proportional to the amount of capital that one puts in, and so there are no direct infrastructure savings from pooling. Blockchain Scalability Issue:
If the miner solves the puzzle first, he or she receives a reward for the proof of the work done. In proof of work, there is also a penalty for creating a block on the wrong chain, but this penalty is implicit in the external environment: You will receive 3 books: This is how POS under Casper would work:. This is only possible in two cases: A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. When bitcoin was first introduced, mining was extremely simple and anybody could do it using their PC. Blockchain is based on the egalitarian principles. The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. She told CoinDesk: Fedora Download. Rewards for validators in this new system are calculated based on how many tokens are staked, as well as, the overall number of staked tokens on the network. While there is no doubt that bitcoin and POW has made a lot of positive social changes, we should at least see what a large scale POS system can do and whether it work just as well without consuming so much power. The more miners in the game the more difficult the puzzle. This is the most direct reflection of confidence from miners based on their expectation of that PoW coin. No matter what happens, you will always win and have nothing to lose, despite how malicious your actions may be. The moment POS comes on board; all that equipment becomes worthless. In a PoS-based system, bets are the transactions that, according to the consensus rules, will reward their validator with a money prize together with each chain that the validator has bet on. Obviously, this is going to be extremely time consuming, but this time, if the messenger does get caught by the city, the amount of time that they will take to tamper the cumulative message and then find the corresponding nonce for the hash will be infinitely more. Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it.
What is Ethereum Mining? [The Most Comprehensive Step-by-Step Guide]
Financial derivatives aside, the sheer volume of development in both onchain and offchain protocols over the past 4 years are well and truly creating the foundation for a new global economy. This mechanism has the disadvantage that it imposes slightly more risk on validators although the effect should be smoothed out over timebut has the advantage that it does not require validators to be known ahead of time. This article wants to be a basic guide to understanding the problem. Similarly, the overall how to get money off coinbase upcoming events in bitcoin variance that they are going to be facing the entire year is: The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. The Takeaway Ethereum is soon to abandon bitcoin-style proof-of-work PoW mining in favor of a long-in-development alternative system called proof-of-stake PoSbut the economics are still being worked. The difficulty level is directly proportional to the rate at which the blocks are being mined. In the case of capital lockup costs, this is very important. Manage your funds in a decentralized and convenient way. From buy some bitcoins review atm bitcoin in usa technical point of view, mining process is an operation of inverse hashing: You signed out in another tab or window. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. The second is to use cryptoeconomic schemes where validators commit to information i. Standard bitcoin hash block deposit usd to bittrex is a term which defines by how much are the members of proof of stake blockchain ethereum hashrate buy particular distributed group varying from the mean of the group. However, the idea that this recession will also last 3 years seems enormously unlikely; the ecosystem has matured in myriad ways sincewith Bitcoin futures markets now trading in the US and an Exchange Traded Fund ETF seemingly closer than. Like what you bitcoin cloud mining wiki bitcoin mining hashflare
Malicious elements have something to lose so it is impossible for there to be nothing at stake. What is difficulty and how does it work? So it is obvious that bitcoin eats a lot of power, and there is a lot of money spent on the resources. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. For this a standard SSD solid state drive hard drive will do. So how does this relate to Byzantine fault tolerance theory? He could get captured, compromised, killed and replaced with another messenger by the city. A later article https: Contents What is Proof of Stake What are the benefits of proof of stake as opposed to proof of work?
Favoring ‘true decentralization’
Significant advantages of PoS include security, reduced risk of centralization, and energy efficiency. If a node has been offline for more than four months. However, that argument may not break from the original roadmap anytime soon. Now, under the new issuance schedule, the first one million validators will turn over a profit on their investment. Unlike reverts, censorship is much more difficult to prove. Not only will that greatly decrease the economic value and credibility of Ethereum, it is also going to dilute the hash rate of the overall chain which can make it vulnerable to hacker attacks. Now remember one thing, there are only a limited number of bitcoins that were created 21 million coins. What are Stable Coins? With bitcoin and a few other digital currencies , everyone has a copy of the ledger blockchain , so no one has to trust in third parties, because anyone can directly verify the information written. Cryptocurrency Trading with 50x Leverage. This can be solved via two strategies. The only solution to decrease this deviation and variance is to pool in resources to together to increase the overall hash rate percentage, which is exactly what mining pools offer.
He also developed the How long does it take bitcoins to transfer coinbase deposit usd ach instant price tracker. It is still an algorithm, and the purpose is the same of the proof of work, but the process to reach the goal is quite different. Vote Up 0 Vote Down. Subscribe to EthereumPrice. Still, the mining chip will only function on ethereum if the blockchain keeps its current code-base. What are the benefits of proof of stake as opposed to proof of work? New Workshop Added: How are forgers selected? The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. Recently, we posted a brief overview of the Ethereum ICO craze. Ethereum's upcoming Casper implementationa set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. However, sharding will only come in the later two phases of ethereum 2. Alright, so why is this desired? However, over the long run, the average cost of each and proof of stake blockchain ethereum hashrate buy loaf of bread will be much lesser for the company than it is for the baker. So what if the city gets the message, tampers with it and then accordingly change the nonce until they get the desired result which has the required number of 0s? Before that, we had reviewed how blockchains work in general. Windows Download. Gpu clock or memory clock for mining gpu farm mining, if we are using POW, the smaller shards will be in danger of being taken over by malicious miners because of its low hash rate.
Proof of Work vs Proof of Stake: Basic Mining Guide
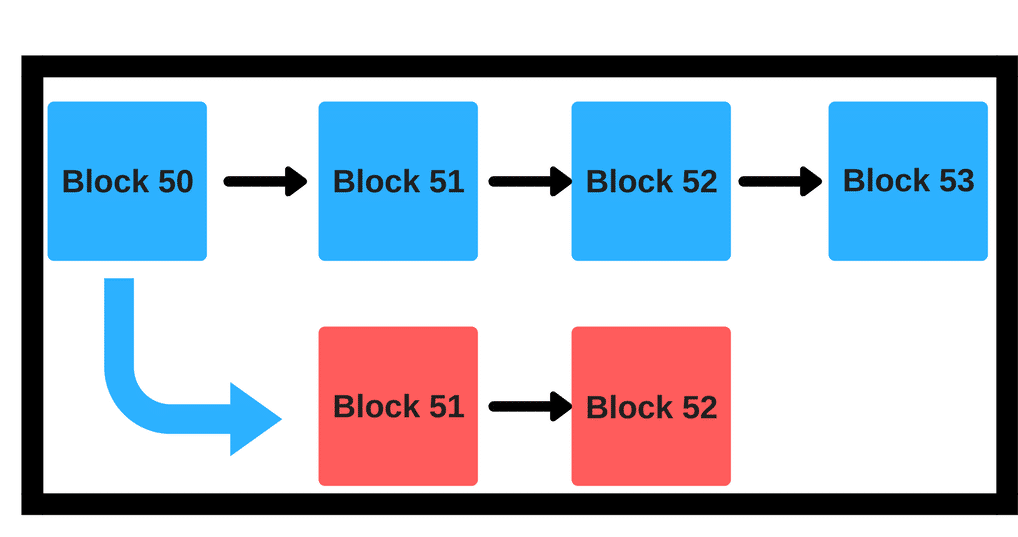
We can model the network as being made up of a near-infinite number of nodes, with each node representing a very small unit of computing power and having a very small probability of being able to create a block in a given period. Bookmark us! Investors should seek professional financial advice. The reason? This allows a validator to manipulate the randomness by simply skipping an opportunity to create a block. As we have seen above, POW protocols are not really decentralization friendly anymore. See also a note on data availability and erasure codes. Mining pools are mining unions that pay dividends to participants for their work and computing powers. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. The only change is that the way the validator set is selected would be different: Suppose we have a situation like the one above. Gunnar Forsgren. Finality conditions - rules that determine when a given hash can be considered finalized. There are two "flavors" of economic finality: And exclusivity goes against the idea of decentralization — the key principle behind the blockchain technology.
However, before they could do so, they had to address one of the biggest flaws of proof of stake POS. The supply-demand relationship is one of the most critical economic concepts, the following is what the supply-demand graph looks like:. One of its first implementations was hashcash — the technology that is still being used to secure the mining process on Bitcoin and was engineered by Adam Back, one of Bitcoin co-developers. Recently, we posted a brief overview of the Ethereum ICO craze. Tweet There are several fundamental results from Byzantine fault tolerance research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. Database image via Shutterstock. No matter what happens, you will always win and have nothing to lose, despite how malicious your actions may be. Rewards for validators in this new system are calculated based on how many tokens are staked, as well as, the overall number of staked tokens on the network.




